Enumerating Domain Trusts in Active Directory
Understanding Active Directory trusts within domains and forests using PowerView
Domain Trusts are relationships that allow communications between domains within one forest or multiple forests. In an Active Directory environment, these relationships allow users and groups to share resources within the organization’s networks.
Some trusts are generated automatically, like Parent-Child and Tree-Root trusts, allowing users of the same forest to share resources together. While others, like External and Realm trusts, must be established manually to access the intended resources, usually located on a different forest. Each trust type can either have One-way or Two-Way directions.
This post will discuss Active Directory domain trusts and their enumeration using the PowerView script. The demonstration steps will be on the Pentester Academy Active Directory Lab by Nikhil Mittal associated with the CRTP course.
$_Trust_Directions
- One-Way trust allows the resources within one domain/forest to be accessible to only specified trusted domains/forests. That trust doesn’t reciprocate; it is only one-way. It is like, “I trust you, but you don’t trust me.”
Let’s look at the diagram below; Domain 2 has a one-way trust to Domain 1. That means all resources within Domain 1 are permitted to access the resources of Domain 2 but not vice versa (domain 2 cannot access domain 1) 🚫.
The arrow points towards who can access the resources with the established trust.
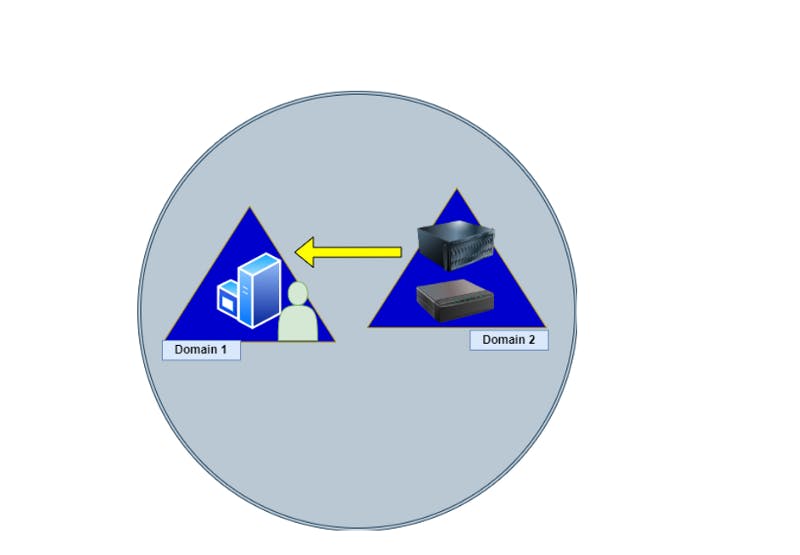
Figure 1 — shows one-way trust
- Two_Way trust allows sharing resources in both directions, like in Figure 2. “We trust each other” ✔️.
Domain 1 shares resources both ways with Domain 2,and vice versa.
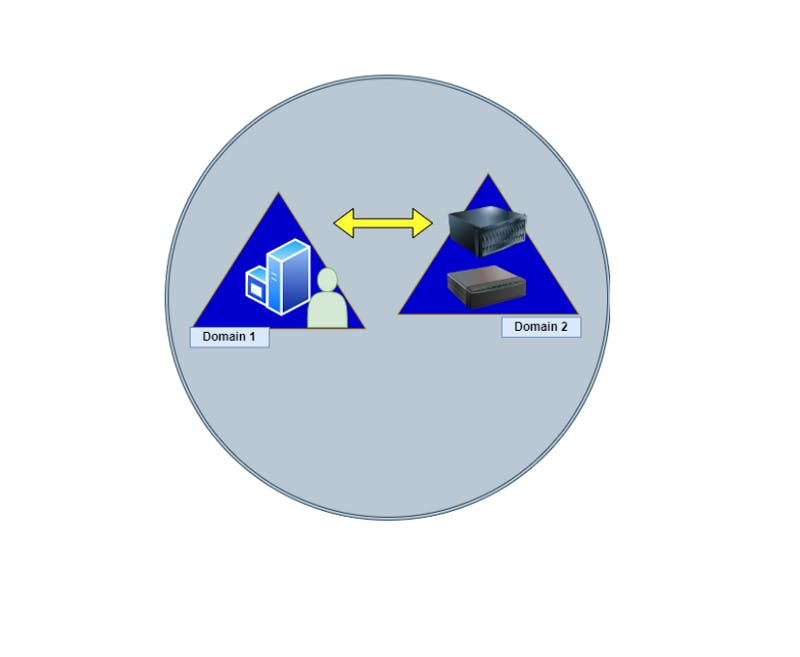
Figure 2 — shows two-way trust
$_Trust_Types
Transitive Trust:
The type of trust extended outside the domain’s boundary to facilitate sharing resources within other domains in the same forest. Some trusts are automatically generated when created, such as the Parent-Child, and Tree-Root trusts with two-way direction.
Others are created manually, like with the Forest and Shortcut trusts. These trusts can either be one-way or two-ways.
In the below diagram, we see that “Forest 1” has a transitive 2-way direction to “Forest 2”, which means that all domains within “Forest 1” are accessible to “Forest 2” and the other way around. The same applies inside the forests, on the tree-root and parent-child levels.
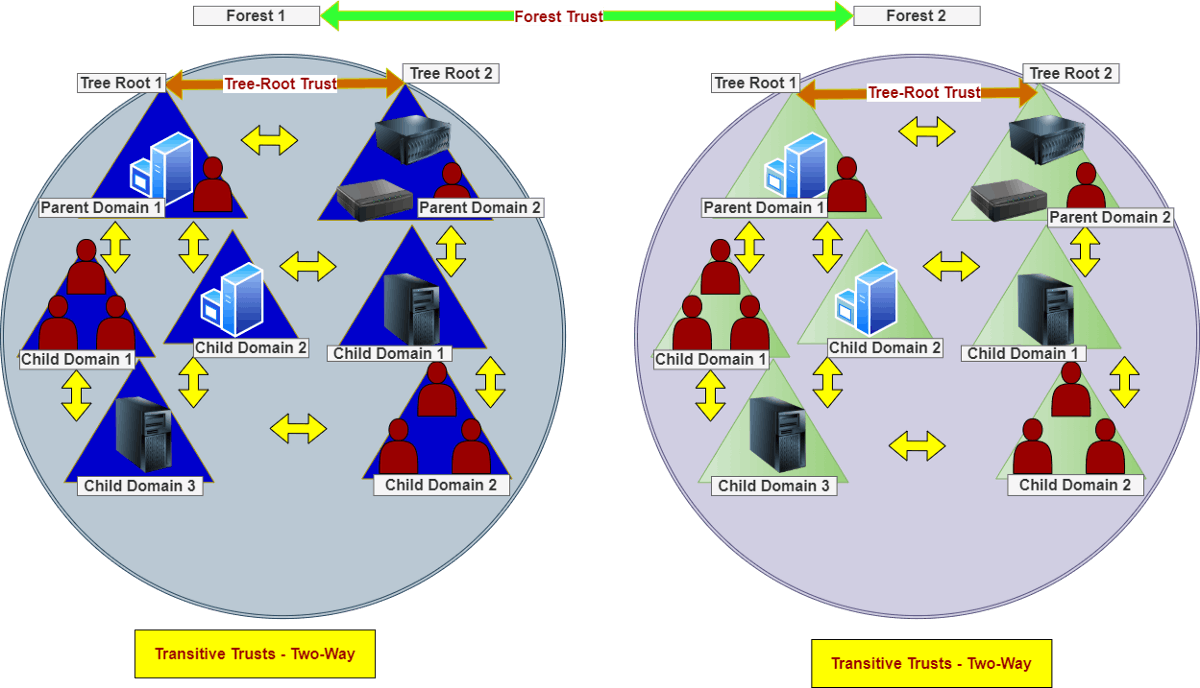
Figure 3 — Transitive Trusts — Forest, Tree-Root and Parent-Child
Non-Transitive Trusts
The type of trust that cannot be extended. It is created manually as a one-way trust to access resources residing on another domain in an untrusted forest. External and Realm (non-windows AD domains) trusts are examples of non-transitive trusts.
The diagram below shows one-way external trust between “Domain 2” in “Forest 2” and “Forest 1”. The arrowhead indicates the access direction. In this case, Forest 1 users have access to Domain 2 in Forest 2 only. Domain 2 in Forest 2 has NO access to Forest 1.
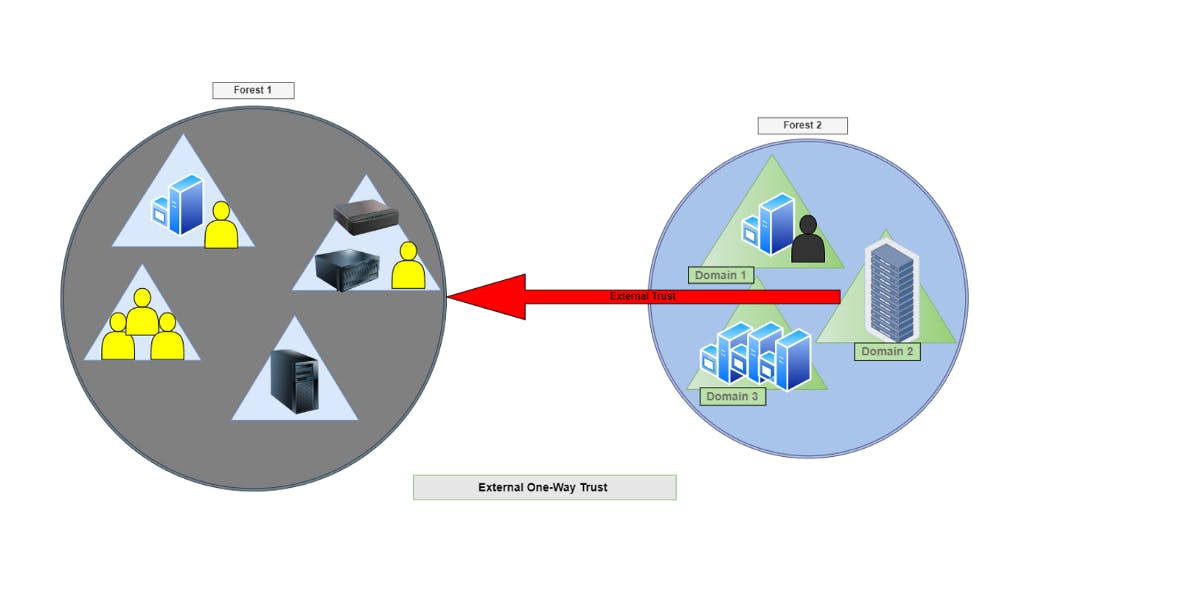
Figure 4 — External Non-Transitive Trust between Domain 2 and Forest 1
🔍$_Enumeration_Steps
Now that we understand the types of trusts in the Active Directory world, let’s start enumerating them within the given environment.
◼️Get Forest Details
First, we start with getting information about the current forest using the Get-NetForest cmdlet alone or using the Forest parameter to specify forest name.
Get-NetForest
Get-NetForest –Forest Forest Name
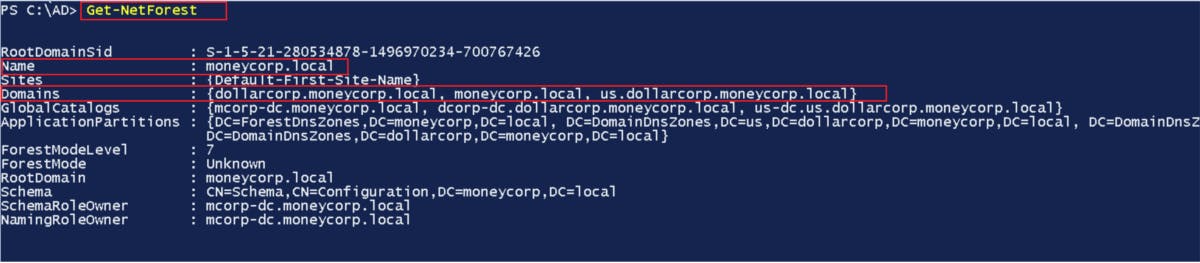
Figure 5 — shows the available trusts for forests
The command returns the current forest name “moneycorp.local” and the available domains within the forest (moneycorp.local, dollarcorp.moneycorp.local, and us.dollarcorp.moneycorp.local).
◼️ Map Domain Trusts
Run the Get-NetDomainTrust cmdlet to get the available trusts within the current or any other trusted domain in the same forest or external. As long as we have the trusts established, we can enumerate them.
Get-NetDomainTrust
Get-NetDomainTrust –Domain [Domain Name]

Figure 6— shows all available trusts of the current domain
The above screenshot shows that the existing domain “dollarcorp.moneycorp.local” has 3 trust relationships:
- Transitive, 2-way trust with its Forest “moneycorp.local.”
- Transitive, 2-way trust with its child domain “us.dollarcorp.moneycorp.local.”
- and an External 2-way trust with another Forest called “eurocorp.local.”
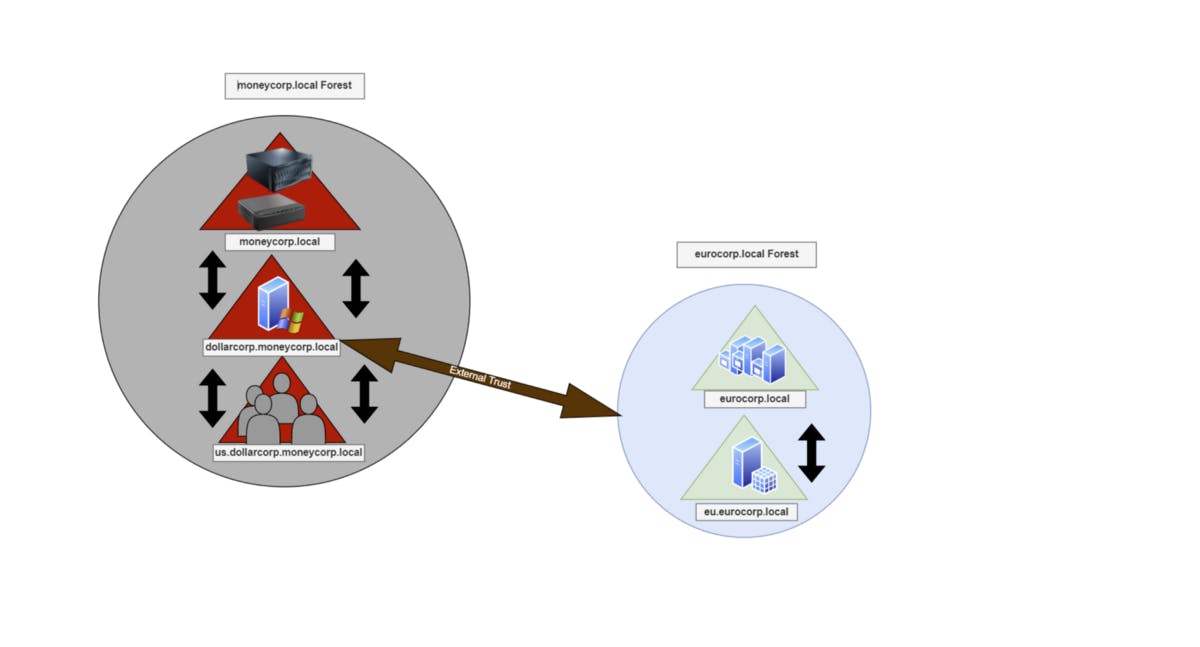
Figure 7 — shows the Dollarcorp.local domain trusts
◼️ Get Domains Structure
To get the structure and hierarchy of the domains within the current or a specified forest, we can run the Get-NetDomainForest cmdlet alone or with the Forest parameter.
Get-NetForestDomain
Get-NetForestDomain -Forest [Forest Name]
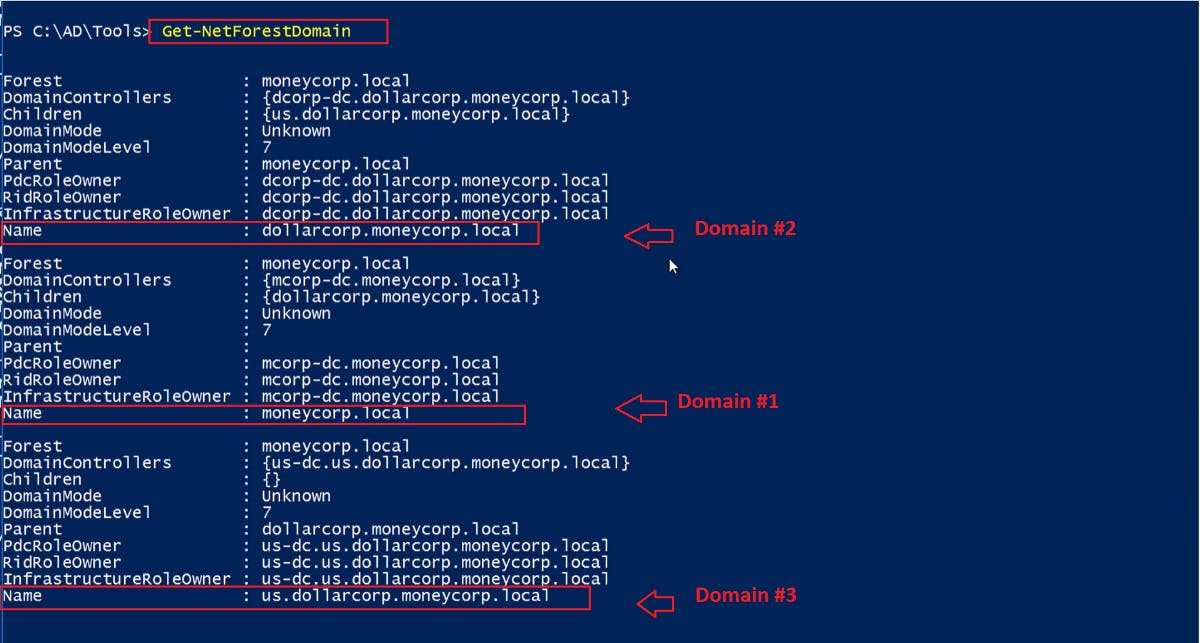
Figure 8 — shows the hierarchy of the available domain within a forest
The above results show that within our forest, “moneycorp.local” is the root domain “moneycorp.local” because it doesn’t have any parent domains, and its child domain is “dollarcorp.moneycorp.local”.
Also, the “us.dollarcorp.moneycorp.local” domain is the child of the “dollarcorp.moneycorp.local” domain.
moneycorp.local > dollarcorp.moneycorp.local > us.dollarcorp.moneycorp.local
This diagram represents the structure of the moneycorp.local forest.
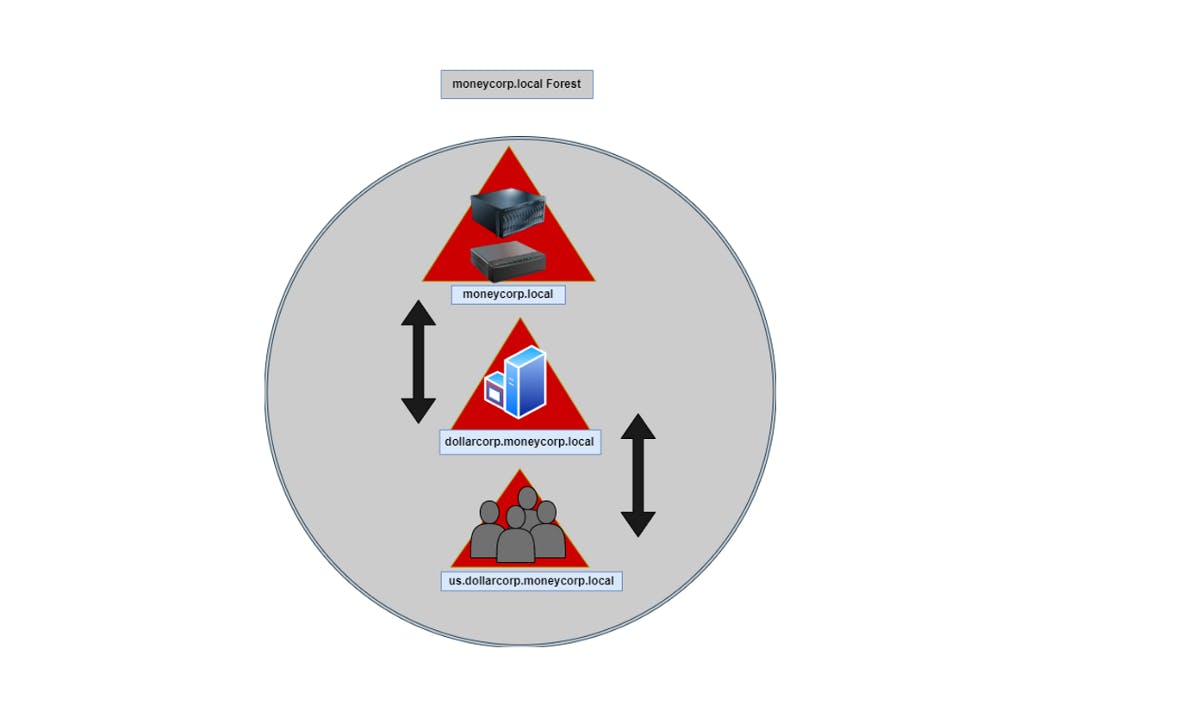
Figure 9 — shows the domains structure within moneycorp.local forest
That’s all for today; we learned about Active Directory trusts and how to map these trusts with the available domains within a given forest using the PowerView enumeration script.
Thanks for reading !!
🔔 I included the AD-module commands in the Notion bucket as an alternative to PowerView. All of the used commands can be found at R3d-Buck3T — (Active Directory — Trusts Enumeration with PowerView and AD-Module)
📚$_References
Attacking and Defending Active Directory Lab
Active Directory Spotlight: Trusts — Part 1. The Mechanics
Active Directory: My Way (Part 1)
Active Directory Spotlight: Trusts — Part 1. The Mechanics
Active Directory Spotlight: Trusts — Part 2. Operational Guidance
Trust Relationships within Active Directory Directory Services

